Platform
Channels

Health Insurance Portability and Accountability Act

ISO 27001:2013 Certification

ISO 27018:2019 Certification

SOC 2 Type II Compliant



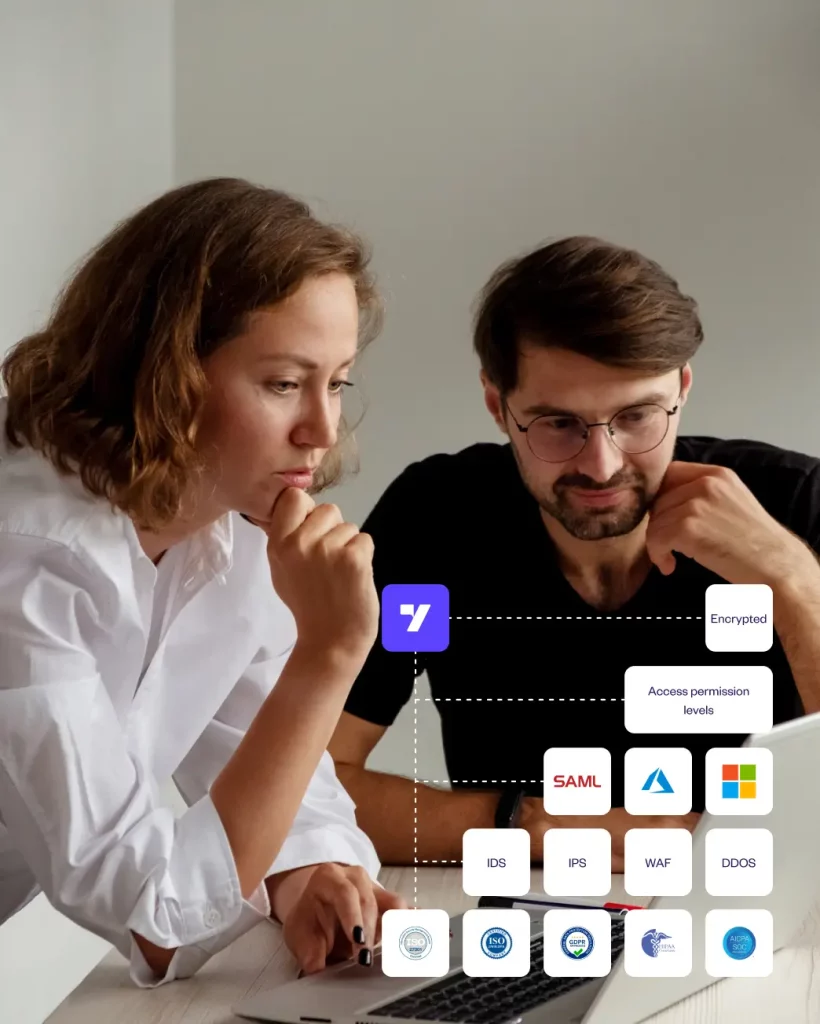
For starters, our platform can be accessed by authorization with user-level access defined. We leverage industry-standard SSO solutions to grant company users access to their company’s bot project and integrations. We support Google SSO, Microsoft SSO, ADFS & Azure AD at the platform level. In addition to that, at the bot level, we support AD, LDAP, SAML and have standard support for OAuth2.
We enable role-based access permission levels within the platform to be set for your teammates. Permissions can be set for roles such as developer, admin, tester, engagement manager, insights, and analytics; wherein users can have permission to change workflow, integrations, databases, bot training, intent mapping, and more, depending on the access granted.
Yellow.ai enforces a password complexity standard and credentials are encrypted using a salted hash (SHA -256).




The Yellow.ai services and data are hosted in the US, EU, Singapore, India, Indonesia and UAE. And because data is gold, our platform was built with disaster recovery in mind. All of our infrastructure and data are spread with N+1 availability zones and will continue to work should any one of the data centers fail. Fingers crossed.
All the data in transit to and fro the platform is SSL TLS 256 encrypted (HTTPS). And to keep access in check, our keys are maintained in Vaults, and the same are recycled every quarter.
Yellow.ai uses 3rd party security tools to continuously scan for vulnerabilities. Our dedicated security team members respond to issues raised. In fact, every year, we engage third-party security experts to perform detailed penetration tests on the chatbot platform.
For complying with various countries and their data laws, we also offer redaction/masking of PII/sensitive information on the data layer of the yellow.ai platform. We’ve also got you covered for WAF, DDOS, IPS & IDS.
All of our servers are within our own virtual private cloud (VPC) with network access control lists (ACLs) that prevent unauthorized requests from getting to our internal network.
